Establish secure private connections for HCP Vault Dedicated for multi-cloud architectures
Multi-cloud architectures using HCP Vault Dedicated present a common networking challenge: maintaining secure, private access to Vault services without public internet dependencies.
Discover secure multi-cloud connectivity patterns for integrating multi-cloud workloads with HCP Vault Dedicated. Even though this blog focuses on setting up HCP Vault Dedicated in AWS and making vault connectivity accessible to Azure, a similar pattern can be used across other cloud providers, such as making HCP Vault Dedicated accessible to GCP through VPN.
This blog post describes how to implement AWS Transit Gateway with site-to-site VPN, explores alternative approaches including AWS PrivateLink and VPC peering, and explains the decision criteria for choosing the right approach.
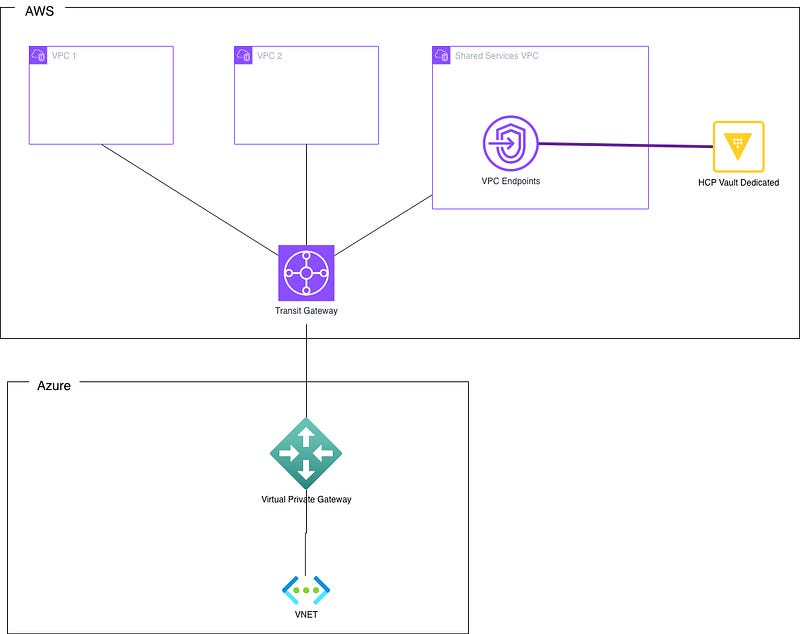
Architecture
The Transit Gateway approach provides transitive routing capabilities, enabling Azure VNets to directly access HCP Vault Dedicated AWS infrastructure once the connectivity is established.
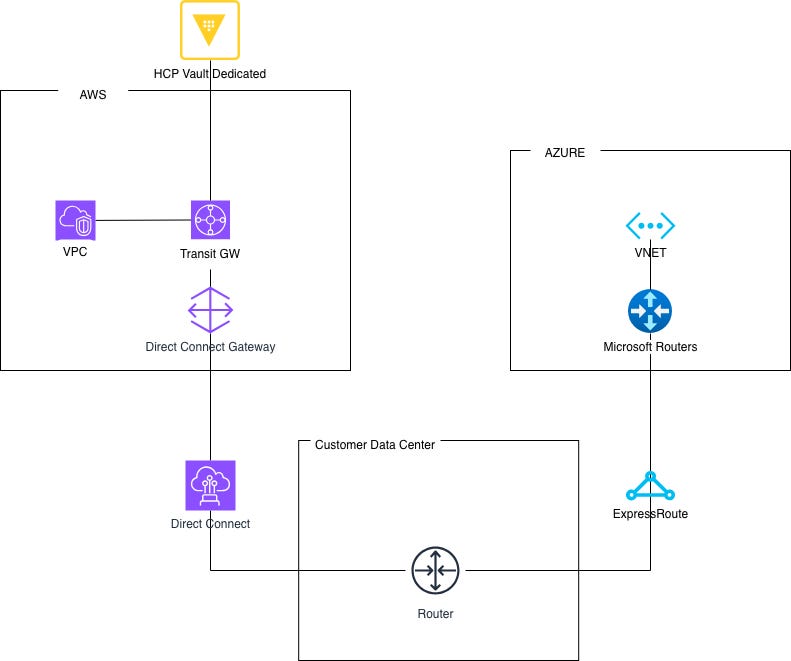
Figure 1 shows organizations already maintaining dedicated connections between datacenters and cloud providers. Azure ExpressRoute or AWS Direct Connect can be integrated into this architecture to provide end-to-end private network connectivity, making it the preferred approach from a security perspective.
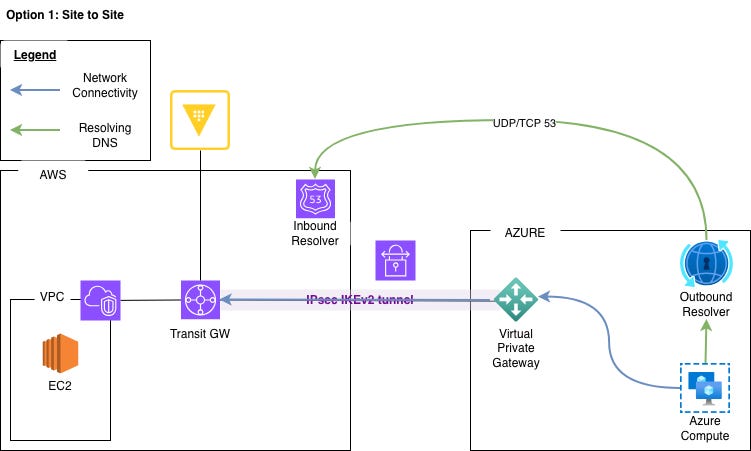
Figure 2 illustrates organizations without dedicated connections, where site-to-site VPN provides an alternative solution. While VPN traffic traverses the public internet, IPsec tunnels encrypt all data in transit, maintaining confidentiality and integrity. The details are described in this AWS blog post.
Since this blog focuses specifically on the site-to-site VPN implementation, we’ll concentrate on the architecture shown in Figure 2.
Setting up site-to-site VPN with a transit gateway
Site-to-site VPN key components are:
1. AWS Transit Gateway (TGW): Acts as a network hub to centralize routing between AWS VPCs and external networks.
2. Site-to-Site VPN: Creates encrypted tunnels between AWS and Azure
3. Azure Private DNS Resolver: Resolves HCP Vault Dedicated private endpoints
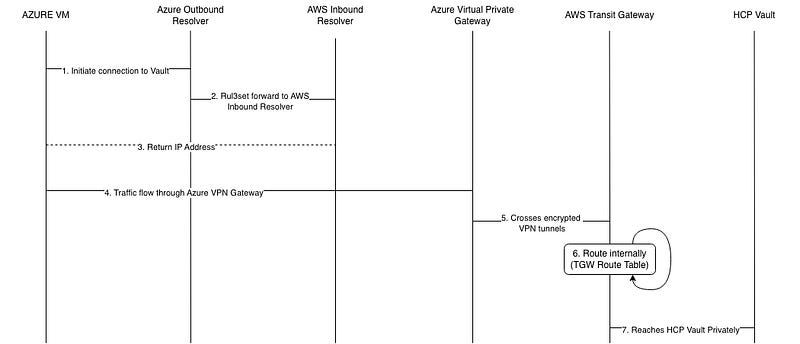
High-level network flow explained
1. Azure VM initiates the connection to Vault
2. Azure ruleset forwards the DNS to AWS Route53 (Inbound Resolver)
3. The IP address is returned
4. Traffic flows through site-to-site VPN from the Azure VPN Gateway
5. Traffic crosses encrypted VPN tunnels from Azure VPN Gateway to AWS Transit Gateway
6. Within AWS Transit Gateway, it uses the internal route table to identify the routing
7. Traffic reaches the HCP Vault Dedicated private address
If you are interested in deploying and trying out site-to-site VPN. You can refer to the GitHub repository available at: https://github.com/jessicaahm/hcpvault
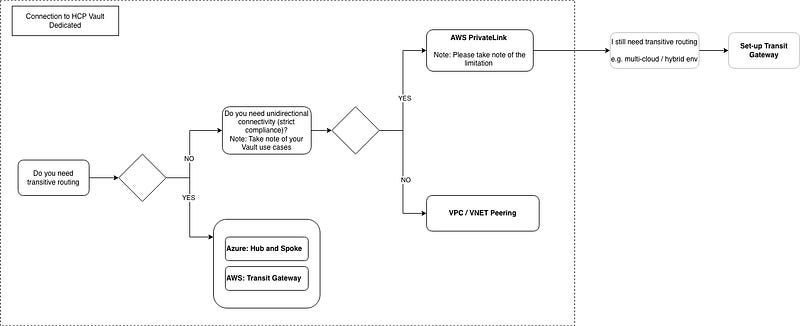
Alternative approaches and limitations to Transit Gateway
Besides using a transit gateway to connect to HashiCorp Virtual Network (HVN), users can choose between AWS VPC Peering and AWS PrivateLink.
When should I use PrivateLink?
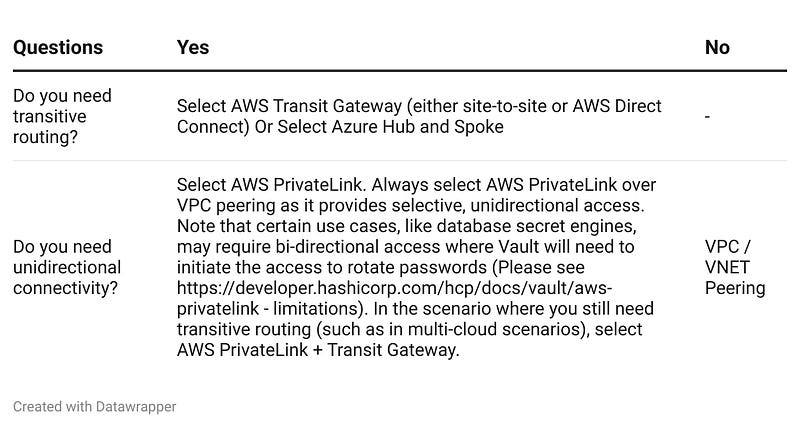
Announced at HashiConf 2025, PrivateLink strengthens your security posture by enabling access to HashiCorp Vault Dedicated using private IP addresses as if the service resides within your own VPC. Furthermore, some organizations may have compliance requirements to use PrivateLink.
This approach delivers several key advantages:
· Traffic remains entirely within the AWS private network, eliminating exposure to internet-based threats
· Simplified management with no route table or firewall configuration requirements
· Eliminates CIDR overlap concerns and VPC peering complexity
· Optimized for unidirectional, service-specific access rather than full network connectivity
· Simpler connectivity without managing multiple route tables or peering relationships
For more details, refer to the official AWS PrivateLink documentation.
What if I still need transitive routing for my multi-cloud environment, but I need to use PrivateLink for compliance reasons?
If you still need transitive routing and need to use AWS PrivateLink, you can still set up the AWS Transit Gateway in your environment and use AWS PrivateLink to connect to HCP Vault Dedicated.
Conclusion
This blog walked you through the architectural patterns of connecting to HCP Vault Dedicated in a multi-cloud environment. Once you have made your decision, refer to the HashiCorp official documents to start setting up the connectivity between your private environment and HCP Vault Dedicated.
If you’re still weighing the pros and cons of different connectivity options, the following chart provides a clear comparison to guide your decision: